Thwarting Obfuscated Malware for Smart Devices
Differential fault analysis, as implemented by Alterdroid, is a powerful and novel dynamic analysis technique that can identify potentially malicious components hidden within an app package.
Authors
This work results from my PhD done under the supervision of Juan E. Tapiador & Pedro Peris-Lopez at Universidad Carlos III de Madrid, and the visiting I did to the research group of Dr. Roberto Di Pietro at Università degli Studi di Roma Tre between September and December 2012.
More information about the authors is listed bellow:
Publications
Publications that arise from this work:
Differential Fault Analysis for thwarting obfuscated malware
Detecting malware in mobile applications has become increasingly complex as malware developers turn to advanced techniques to hide or obfuscate malicious components.
Such components are often hidden outside the app’s main code components, as these might be subject to static analysis by market operators.
The key idea consists of analyzing the behavioral differences between the original app and an altered version of it where a number of modifications (faults) have been carefully introduced.
Such modifications are designed to have no observable effect on the app execution, provided that the altered component is actually what it should be and does not have any hidden functionality.
Alterdroid a tool for applying Differential Fault Analysis
Alterdroid is a dynamic analysis tool that compares the behavioral differences between an original app and numerous automatically generated versions of it containing carefully injected modifications.
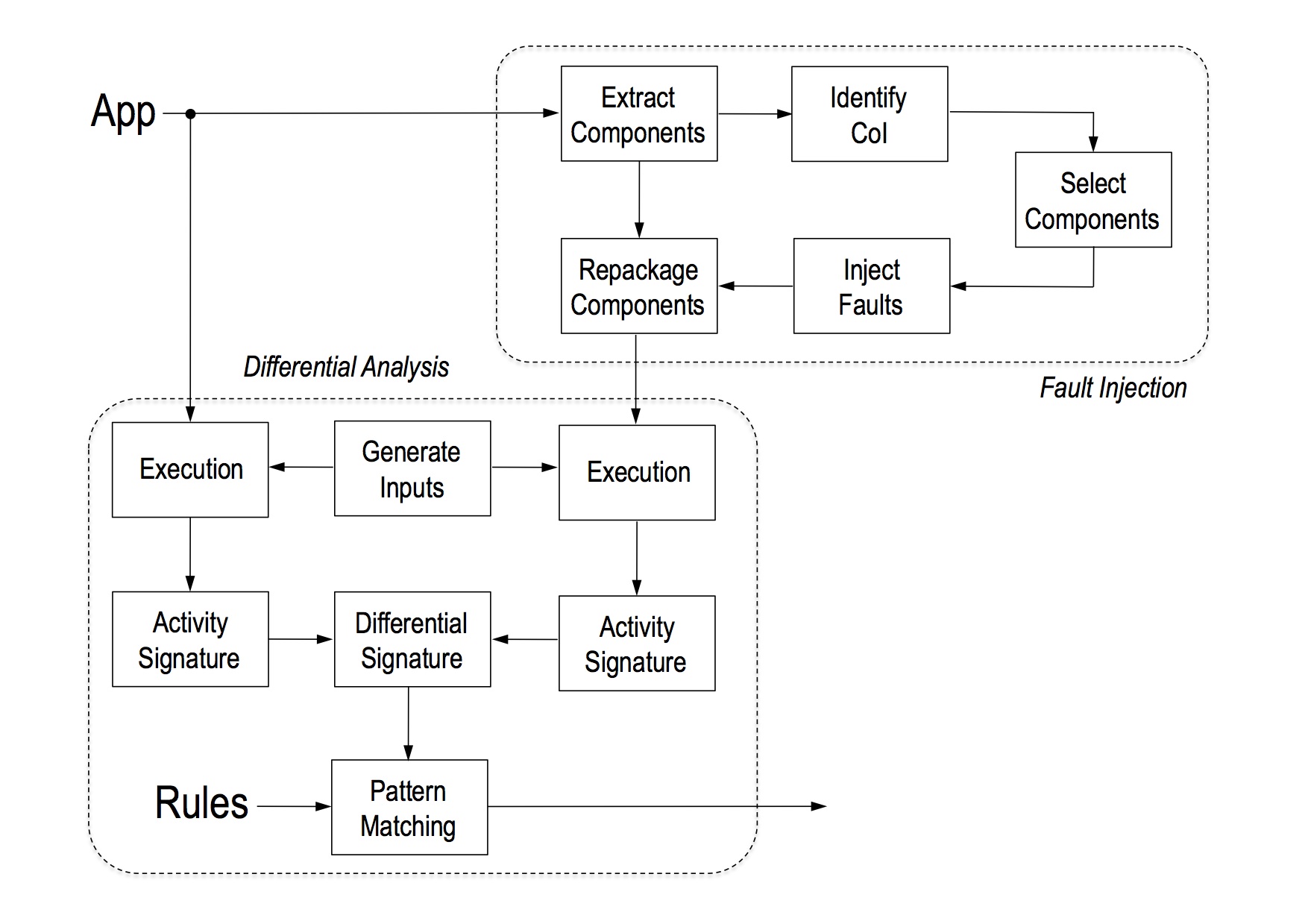
At high level, Alterdroid has two differentiated major components: fault injection and differential analysis. The first one takes a candidate app –the entire package– as input and generates a fault-injected one.
Both the original and the fault-injected apps are then executed under identical conditions (i.e., context and user inputs), and their behavior is monitored and recorded producing two activity signatures.
The differential signature is finally analyzed through a pattern-matching process driven by rules that relate different types of hidden functionalities with elements found in the differential signature.
Analytical results
To illustrate how market operators and security analysts can use Alterdroid to help analyze complex obfuscated mobile malware, we present three case studies of malicious Android apps: DroidKungFu (DKF), AnserverBot (ASB), and GingerMaster (GM).
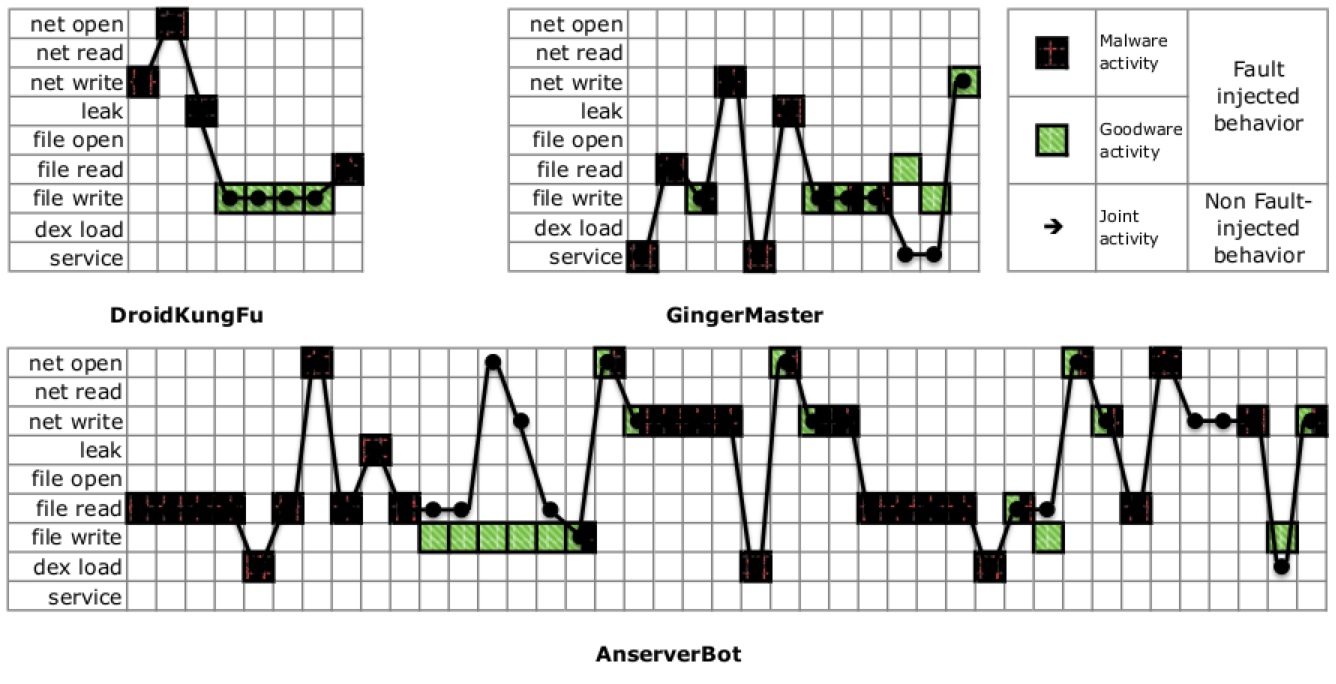
Figure shows the differential behavior reported by Alterdroid over a two-minute period. Activities launched by the original piggybacked app correspond to the full plot, while the behavior after fault injection is indicated by the green (legitimate app) and red spots (DKF).
We tested Alterdroid against a dataset composed of around 300 obfuscated malicious apps, grayware, and goodware.
A summary of the experimental reports can be found in the publications, and full reports are available here.
We further extended this study to include around 10K samples from GooglePlay, Aptoide, and VirusShare.
Get the tool
Alterdroid is a good complement to static analysis tools, that are focused on inspecting code components, hence possibly overlooking pieces of code hidden in data objects or just obfuscated.
We are currently working on an open-source engineered version of Alterdroid striving on offering an automatic tool for malware analysis.
Source code is available to the research community for fair use:
https://bitbucket.org/gtangil/alterdroid - User Manual
Please, contact me for more information at .
© Copyright 2014 Universidad Carlos III de Madrid. All rights reserved.

